Blockchain technology, at its core, is a decentralized ledger that records transactions across many computers in such a way that the registered transactions cannot be altered retroactively. Each transaction is secured and verified through a consensus mechanism, ensuring that every participant in the network agrees on the transaction’s validity. This transparency and security have made blockchain popular in various fields, from finance to supply chain management.
Imagine a massive digital spreadsheet duplicated thousands of times across a network of computers. This spreadsheet is constantly updated and verified. The beauty of blockchain lies in its decentralization and transparency. Unlike traditional databases controlled by a single entity, blockchain is managed by a distributed network, making it highly secure against tampering and fraud.
For more insights on blockchain technology, visit Tech Blog Post.
What is a Hash?
So, what exactly is a hash? In simple terms, a hash is a string of characters generated by passing data through a hash function. It’s like a digital fingerprint for your data. No matter how large or small the input data is, the hash function converts it into a fixed-length string. For instance, the word “hello” might be converted into a long string of numbers and letters.
A hash is unique to the input data, meaning even the slightest change in the input will result in a completely different hash. This property is crucial for verifying the integrity of data. Just as each human fingerprint is unique, a hash uniquely identifies a piece of data.
How Does Hashing Work in Blockchain Technology?
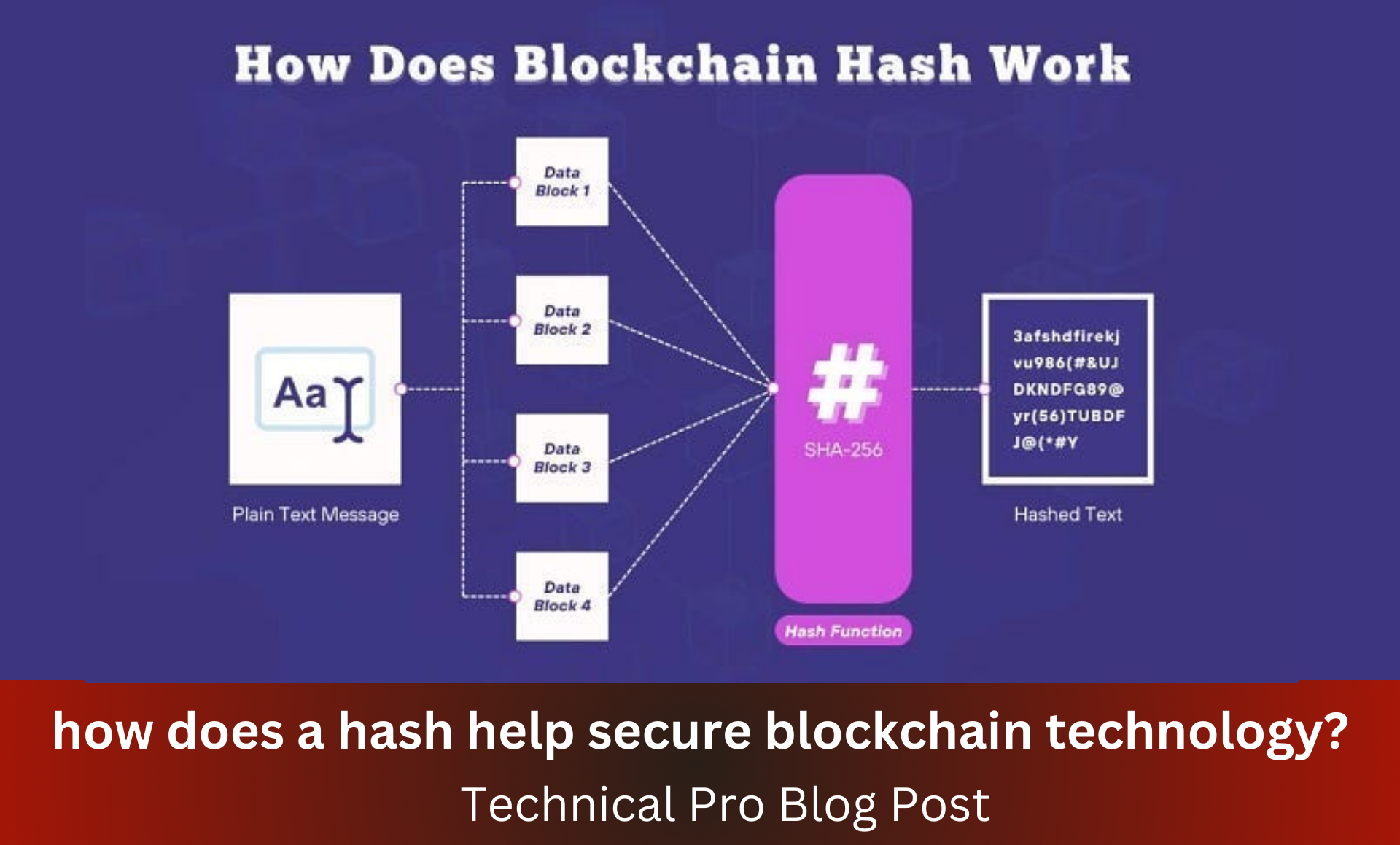
Hashing works by taking input data and processing it through a hash function. This function performs mathematical operations on the data to produce a unique hash value. Imagine a blender: you put your fruits (data) into the blender (hash function), and out comes a smoothie (hash value). No matter how many times you blend the same fruits, you’ll always get the same smoothie. But if you change the fruits even slightly, you’ll get a completely different smoothie.
In technical terms, a hash function takes an input (or ‘message’) and returns a fixed-size string of bytes. The output is typically a ‘digest’ that represents the input data. Even the smallest change to the input will produce a significantly different hash, making it a highly effective tool for data verification.
For example, consider the SHA-256 hash function used by Bitcoin. If you input “Hello, world!” into SHA-256, you get a specific hash. Change it to “Hello, World!” (with a capital W), and you get a completely different hash. This sensitivity to input changes is a critical feature of hash functions in blockchain technology.
The Role of Hashes in Blockchain Technology
Hashes play a vital role in blockchain technology by ensuring data integrity and security. Every block in the blockchain contains a hash of the previous block, a timestamp, and transaction data. This chaining of blocks through hashes is what gives blockchain its name. It ensures that once data is recorded in a block, it cannot be altered without altering all subsequent blocks, which would require consensus from the entire network.
Consider the blockchain as a linked chain of blocks, where each block has a unique hash. If any information in a block is altered, the hash of that block changes, causing a domino effect. Subsequent blocks’ hashes would no longer match, immediately signaling tampering. This interdependence of blocks through hashes makes the blockchain incredibly secure and immutable.
For more detailed articles on how blockchain technology works, visit Tech Blog Post.
Hash Functions in Blockchain Technology
Hash functions are mathematical algorithms that take an input and produce a fixed-size string of bytes. The output, known as the hash value, is unique to each unique input. In blockchain technology, hash functions are used to create the hash of a block. Common hash functions include SHA-256 (used by Bitcoin) and Keccak-256 (used by Ethereum).
SHA-256, short for Secure Hash Algorithm 256-bit, is one of the most commonly used hash functions. It takes an input and produces a 256-bit (32-byte) hash value, typically rendered as a 64-digit hexadecimal number. This function is part of the SHA-2 family of cryptographic hash functions designed by the NSA.
Ethereum, on the other hand, uses Keccak-256, a variant of the SHA-3 cryptographic hash function. Despite differences in their algorithms, both SHA-256 and Keccak-256 provide high levels of security, making them suitable for blockchain applications.
Cryptographic Hash Functions
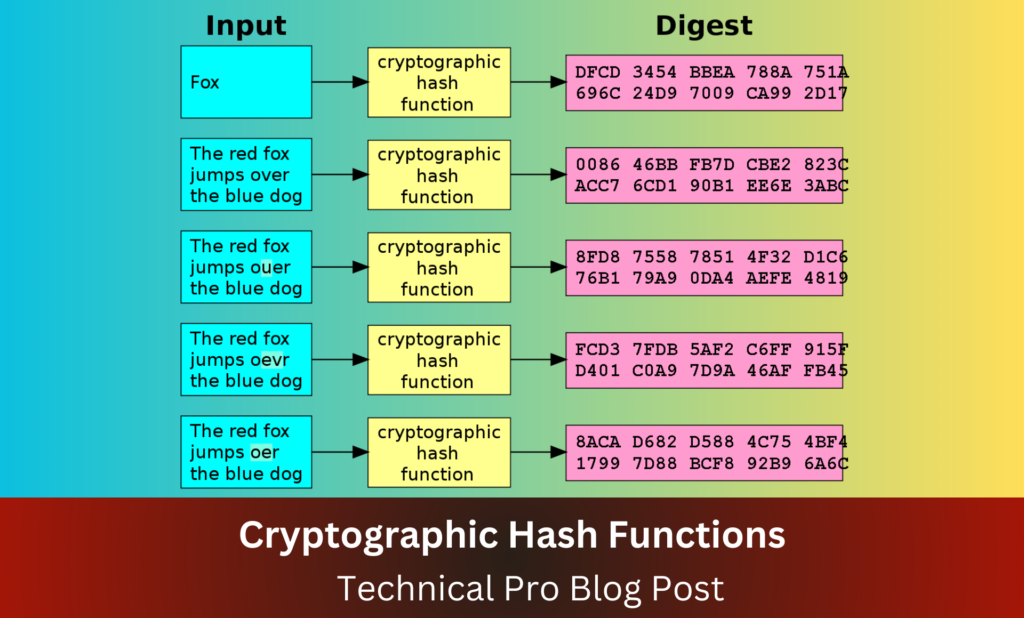
Cryptographic hash functions are a specific type of hash function designed to be secure. They have several important properties: they are deterministic, quick to compute, and it is infeasible to generate the original input data from its hash value (pre-image resistance). Additionally, a small change in input data results in a significantly different hash value (avalanche effect), and it is infeasible to find two different inputs that produce the same hash value (collision resistance).
These properties make cryptographic hash functions ideal for securing blockchain data. The deterministic nature ensures that the same input will always produce the same hash, while the avalanche effect ensures that even minor changes in input drastically change the output, enhancing security. Pre-image and collision resistance prevent attackers from forging data or finding two different inputs that produce the same hash.
To learn more about cryptographic hash functions, check out Tech Blog Post.
Immutability in Blockchain Technology
Immutability refers to the unchangeable nature of data once it has been recorded on the blockchain. This is crucial for maintaining trust and security in the system. Hashes ensure immutability by linking each block to its predecessor. If someone attempts to alter a block, it would change the hash of that block and break the chain, immediately signaling tampering.
This immutability is a key feature that sets blockchain apart from traditional databases. In a traditional database, data can be altered or deleted, which opens the door to fraud and errors. In contrast, blockchain’s immutability ensures that once data is entered, it is permanent and unalterable. This feature is particularly valuable in industries where data integrity is paramount, such as finance, healthcare, and supply chain management.
Ensuring Data Integrity
Data integrity is about making sure the data hasn’t been altered or tampered with. In blockchain, hashes are used to verify the integrity of the data in each block. If the data within a block is altered, the hash will change, and this discrepancy will be detected by other nodes in the network, maintaining the overall integrity of the blockchain.
Think of data integrity in blockchain as a tamper-evident seal. When a block is created, a unique hash is generated based on the block’s content. If anyone tries to alter the data within that block, the hash will change, making it clear that tampering has occurred. This mechanism ensures that all participants in the network can trust the data recorded on the blockchain.
Preventing Double Spending
Double spending is the risk that a digital currency can be spent twice. Blockchain technology addresses this problem using hashes and consensus mechanisms. Each transaction is hashed and linked to the previous transaction in the blockchain. This linking and hashing prevent the same unit of cryptocurrency from being spent more than once because each transaction is verified and recorded in a transparent, immutable ledger.
Imagine you have a digital $20 bill. Without blockchain, you might try to spend that $20 bill twice by duplicating the digital file. Blockchain prevents this by recording each transaction in a block, which is then hashed and linked to the previous block. This creates a secure and transparent record of transactions, ensuring that each unit of cryptocurrency can only be spent once.
For more on how blockchain prevents double spending, visit Tech Blog Post.
Consensus Mechanisms and Hashes
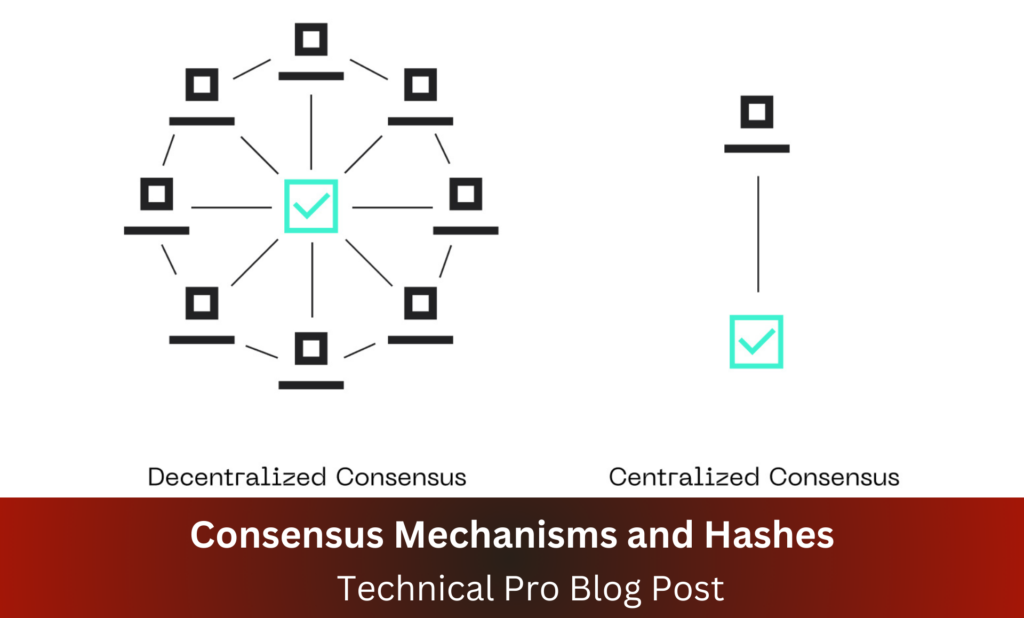
Consensus mechanisms are protocols used by blockchain networks to agree on the validity of transactions. They play a critical role in maintaining the security and integrity of the blockchain. Common consensus mechanisms include Proof of Work (PoW) and Proof of Stake (PoS). In PoW, miners compete to solve complex mathematical problems (hash functions) to add new blocks to the blockchain. In PoS, validators are chosen based on the number of tokens they hold and are willing to “stake” as collateral.
Proof of Work is the consensus mechanism used by Bitcoin. Miners compete to solve cryptographic puzzles based on hash functions, with the first one to solve the puzzle getting the right to add the next block to the blockchain. This process requires significant computational power, which makes it difficult for any single entity to control the network.
Proof of Stake, used by Ethereum 2.0, selects validators based on the number of tokens they hold and are willing to stake as collateral. Validators are randomly chosen to propose and validate new blocks. This mechanism is more energy-efficient than Proof of Work and provides a different approach to securing the blockchain through economic incentives.
Hash Pointers
A hash pointer is a pointer to where some information is stored along with the cryptographic hash of that information. In a blockchain, each block contains a hash pointer to the previous block, creating a chain of blocks. This ensures that each block is linked to the one before it, making it impossible to alter a single block without altering the entire chain.
Hash pointers are essential for maintaining the integrity and security of the Blockchain Technology. They not only point to the location of previous blocks but also contain the hash of the data in those blocks. This dual function ensures that any attempt to tamper with a block will be immediately detectable, as the hash pointer will no longer match the altered block’s hash.
Merkle Trees
Merkle trees, or hash trees, are a way of organizing and verifying data in a blockchain. They allow efficient and secure verification of the contents of large data structures. A Merkle tree is built by hashing pairs of data and then hashing those hashes together until a single hash, known as the Merkle root, is obtained. This structure allows for efficient and secure verification of the data in the tree.
Merkle trees are used in blockchain to ensure data integrity and quick verification. For example, in Bitcoin, Merkle trees allow for the efficient verification of transactions in a block. By using the Merkle root, a node can quickly verify whether a transaction is part of the block without needing to check every transaction individually.
For more on the technical aspects of Merkle trees, check out Tech Blog Post.
Security Challenges and Mitigations
Despite the robust security features of hashes and Blockchain Technology, there are still challenges such as the potential for quantum computing to break cryptographic hashes and the 51% attack, where a group of miners controls more than half of the network’s hashing power. Mitigations include using quantum-resistant cryptographic algorithms and developing more decentralized consensus mechanisms.
Quantum computing poses a significant threat to current cryptographic hash functions. Quantum computers can potentially solve complex mathematical problems much faster than classical computers, potentially breaking the cryptographic security of current hash functions. To mitigate this threat, researchers are developing quantum-resistant algorithms that can withstand attacks from quantum computers.
The 51% attack is another major concern. If a single entity or group controls more than 50% of the network’s hashing power, they could potentially rewrite the blockchain and double-spend coins. Mitigating this risk involves promoting decentralization and ensuring that no single entity can gain too much control over the network. This can be achieved through mechanisms like Proof of Stake, which reduces the incentive to control a majority of the network’s resources.
Future of Hashing in Blockchain Technology
The future of hashing in blockchain technology looks promising. Advances in cryptographic research continue to enhance the security features of hash functions. As blockchain technology evolves, we can expect to see even more sophisticated uses of hashes to secure data and transactions. This evolution is crucial for the widespread adoption of blockchain in various industries.
New cryptographic algorithms are being developed to address the limitations of current hash functions. For example, researchers are exploring post-quantum cryptography, which aims to develop cryptographic algorithms that are secure against quantum computing attacks. These advancements will ensure that blockchain technology remains secure and reliable in the face of evolving threats.
Moreover, the integration of Blockchain Technology with other technologies, such as the Internet of Things (IoT) and artificial intelligence (AI), will create new opportunities for the use of hashes. These integrations will enhance the security and efficiency of data verification processes, further solidifying blockchain’s role as a foundational technology for the future.
For updates on the latest developments in blockchain technology, visit Tech Blog Post.
Conclusion
In conclusion, hashes are an integral part of blockchain technology, providing the security and integrity that make it so revolutionary. By understanding how hashes work and their role in the blockchain, we can appreciate the robustness of this technology. Whether it’s ensuring data integrity, preventing double spending, or maintaining immutability, hashes are the unsung heroes keeping blockchain systems secure and reliable.
For more insights on blockchain technology and cybersecurity, visit Tech Blog Post and check out their Cybersecurity Bootcamp in Dallas.
FAQs
1. What is a hash in blockchain technology?
A hash in blockchain technology is a fixed-length string of characters generated by passing input data through a hash function. It acts as a digital fingerprint for the data, ensuring its integrity and security.
2. How does hashing ensure data integrity in Blockchain Technology?
Hashing ensures data integrity in blockchain by producing a unique hash value for each block of data. If the data is altered, the hash value changes, making tampering easily detectable.
3. What are cryptographic hash functions?
Cryptographic hash functions are secure hash functions with properties like pre-image resistance, collision resistance, and the avalanche effect. They are used in blockchain to ensure data security and integrity.
4. How do hashes prevent double spending in blockchain?
Hashes prevent double spending by linking each transaction to the previous one in the blockchain. This chaining ensures that once a transaction is recorded, it cannot be altered or duplicated.
5. What is the role of consensus mechanisms in blockchain security?
Consensus mechanisms in blockchain security are protocols that ensure all participants agree on the validity of transactions. They use hash functions to validate and add new blocks to the blockchain, maintaining its integrity and security.